0patch experts recently came out with a micropatch designed to mitigate a previously unidentified zero-day loophole in Adobe Reader. According to experts, this vulnerability can be abused by cyber criminals by hiding malware inside corrupt PDF files.
These documents would then transfer the target’s NTLM hash to the attacker through a SMB request. All of this can be done remotely which would make detection practically impossible.
The vulnerability was identified and reported by Alex Inführ, a security expert who also published a proof-of-concept and technical details of the problem. According to the report, the XML Form Architecture (XFA) structure was instrumental in crafting the attack. XFA is an integral part of PDF documents and it’s what determines the form and other aspects of the document.
However, cybercriminals can bypass this technique altogether and use an XML-stylesheet instead to achieve the same ends.
Once Adobe detects an XML-stylesheet element containing a HTTP/HTTPS URLs, it usually asks for user confirmation before continuing. But, one can bypass this measure by using UNC paths instead.
It’s interesting to note that this is a similar attack to the “BadPDF” aka CVE-2018-4993 problem that required Adobe to put out fires in November. The vulnerability opened an opportunity for attackers to access users’ NTMLv2 hash through a remotely controlled SMB server that sent the stolen data back to the hacker’s remote PC.
It also allows the document to “call home” by alerting the attacker that the victim has opened the document, thus allowing them to activate their full-scale attack. The hacker would do this by automatically loading yet another corrupted PDF remotely.
The expert who blew the whistle on this flaw tested the Adobe Acrobat Reader DC 19.010.20069 PoC in Windows.
He found that the micropatch worked well in mitigating the attack and that users can use it to eliminate the vulnerability.
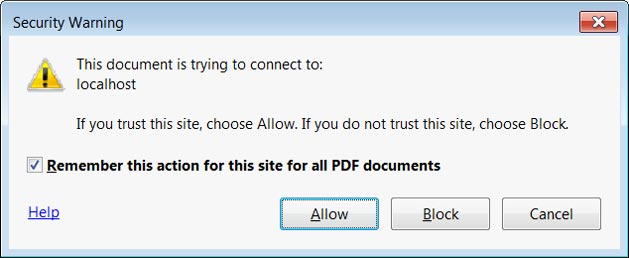
The 0patch micropatch allows the system to display a warning to users whenever they’re exposed to this particular attack. The message from the display warning is as follows, and users must be careful it if it ever appears on their screens:
“This document is trying to access a file on your network. If you trust this document, choose Yes. If you do not trust this document, choose No.”
As you can see, the warning gives the user the opportunity to rebuff the attack thus protecting their information, privacy and file safety.
