Are you a Facebook user? The world’s most popular social media platform is a place to share experiences, catch up with family and friends – and stay in touch with news events around the world.
The Age of Social Media
Since its creation in 2004 as a means of connecting college kids studying at ivy league schools, Facebook has grown into a tech behemoth, with over 2-billion active monthly users – that’s over a quarter of the world’s population!
It took some time for Facebook to catch on with the general public, but when Mark Zuckerberg changed the business model of the platform into a public-facing network, global growth started to surge.
Today, Facebook is a source of news, information, and entertainment for billions of people. The functionality of the platform is what makes it great. Marketers rely on the platform to reach out to their customers, seniors can keep tabs on their grandchildren, and friends can talk about the upcoming warehouse party on the weekend, or discuss the next bid UFC fight or sporting event.
Information – The World’s Most Valuable Commodity
In the digital age, information is everything. How we experience our lives and what we do with our time, all depend on the information available to us daily. When you arrive at work and boot up your computer, you have a wealth of information available at your fingertips.
Companies use information on operations and competitors to control their business activities, governments rely on information and data to keep tabs on international competitors, and people require information to learn about social and professional events occurring around the world.
Gone are the days of using the post and television to keep up with news stories and meet new people. The advent of social media connected every person on the planet. Today, all you need to do to reach anyone, anywhere on the planet – is send them a friend request on Facebook.
Most of us happily share all the details of our life on Facebook, without a second thought to our privacy, or that of others on the platform. We rely on Facebook to regulate the service while giving us the freedom to access the information we choose.
In the modern worlds – information is power, and you’re either informed and aware or left lost in the ether. Access to information increases your opportunity in life, and Facebook offers anyone with an internet connection and a mobile device, the chance to achieve their dreams.
What Happens When You Lose Your Password?
When you sign up for a Facebook account, the system prompts you to enter a password to protect your account from hackers. Password protection is an essential part of online security, and it’s a vital step in signing up for the platform.
Facebook recommends you choose a random password that’s a mix of lower-case and capitals, as well as numbers and special characters. This strategy ensures that people can’t guess your password and gain unauthorized access to your profile.
Facebook offers users the opportunity to link their profile to their email account of cellphone number for easy recovery if they lose or forget their password.
However, what happens when you lose your Facebook password and fail to set up a phone number or email account for recovery purposes?
Maybe someone stole your laptop or mobile device – or you download a virus that crashes your machine. Whatever the reason for the permanent loss of your password, it doesn’t change the fact that you’ve locked yourself out of your Facebook account.
DISCLAIMER – How to Hack Your Facebook Account
This tutorial teaches you what you need to know to break into any Facebook account, from any location in the world. However, the purpose of this guide is not to help you hack into other people’s social media accounts.
Gaining unauthorized access to someone else’s Facebook account is punishable by law. Should you use this information to hack someone’s profile, then you run the risk of being charged under the cybercrimes act, which could land you with a hefty fine, and possible jail time.
While this tutorial discusses methods you can use to hack an account, it does not talk about how to hide your identity online. If you break into another users account, the Facebook team can track your location, identifying you as the hacker.
The information in this article is for ethical and responsible use only, remember – with great power comes great responsibility.
Navigate to The Methods Quickly:
1. Hack Facebook Account Using Software (Brute-Force method)
2. With Phishing Method
2.1. How to Make a Facebook Phishing Page from Scratch
3. Using Keylogger to Hack Facebook Password
3.1. Keyloggers for Windows/Mac
3.2. Keyloggers for Android/iOS
4. With Social Engineering Skills
5. By Password Guessing
6. With Remote Access Trojan Tool
7. Using The Man in The Middle Attack Method
8. By Hiring a Professional
9. More ways explained how to hack a Facebook account
Comparison: What is the Best Method to Hack Facebook Account?
An Extra Tip: What to do if Someone Hacked Your Facebook Account
1. Hack Facebook Account Using Software (“Bruteforce Method”)
 The first and best method of hacking your Facebook account is the “brute-force” method. This method uses specially designed software to crack the password. This software receives automatic updates of the latest passwords, allowing it to run through the list of potential combinations in a few minutes. All you need to do is download the software to your phone or laptop, then run the software and it does the rest for you.
The first and best method of hacking your Facebook account is the “brute-force” method. This method uses specially designed software to crack the password. This software receives automatic updates of the latest passwords, allowing it to run through the list of potential combinations in a few minutes. All you need to do is download the software to your phone or laptop, then run the software and it does the rest for you.
You can find this tool for download on its official website:
www.FBShredder.com
It’s developed by Progressive PST team of coders.
This automated solution is far more user-friendly than the previous method hackers would use of opening a text document, compiling a password list, and using a program to try to access the target account. With the fully automated operation of the new generation of brute-force software, anyone can hack into any account, without specialized hacking knowledge.
The latest version of brute-force software features stealth-mode applications that hide the processes from the view of any user, allowing you to go undetected as you crack the account. These programs spoof your IP, concealing your operations from your ISP and Facebook’s security team. Developers are constantly updating their list of proxies, and provide dozens of clone fake addresses to ensure stealth operation of your hacking tasks. Brute-force software also clears your browser cookies after every session, eliminating the possibility of anyone tracking your use of the software.
The time it takes to hack an account depends on a variety of factors, such as the password strength, efficiency of the hacking software you’re using, and the processing power of your computer or device that’s running the program, as well as the connection speed. We recommend you use a fiber connection or LTE-enabled device to run the program with the best results.
Most versions of brute-force hacking software are available for free download on mobile (Android & iOS), PC (Windows/Linux), and Mac devices.
2. With Phishing Method
After the brute-force method, the next favorite way of hacking a Facebook account – is phishing. Phishing is the bread and butter method for many hackers because it’s so easy to fool the user into blindly handing over their Facebook details, without being aware that they’ve given up their password.
Phishing is responsible for up to 80-percent of all account hacks, and this statistic is not in danger of changing at any time soon – due to its success rate in cracking passwords. Hackers create a faux Facebook login page that looks like the real deal.
The hacker then sends the target an email or text message posing as Facebook admin staff. The communication states that they require the user to log onto their Facebook account for some security reason or to check a text from a friend. The message contains a link to the phishing page, and when users click the link – they end up on the hacker’s page, instead of the legitimate Facebook login page.
The victim then enters their username and details. In many cases, smart hackers will link their faux phishing page to the Facebook site, allowing the victim to visit their page after they log in. This strategy leaves the mark unaware of any suspicious activity and provides the hacker with plenty of time to access the page and do whatever they want to the account – including changing g the password to lock out the user.
Since Facebook links to Instagram, it’s possible for the hacker to gain access to your Instagram account as well. Hackers steal your data and sell it on the dark web to users that commit cyber crimes such as fraud and identity theft.
Setting up a phishing page is a complicated process, and most hackers require specialized software tools to construct phishing scams. However, it’s possible to create a phishing page, as long as you know what you’re doing.
Hacking a Facebook accounts with phishing method is also well explained in this video:
2.1. How to make a Facebook Phishing Page from Scratch
Designing a phishing page is not as challenging as you think, all you need is a PC, an internet connection, willing to learn some basics of HTML language available here, a web host account, and a Notepad. If you have these tools on hand, you can follow this method to set up your first Facebook phishing page.
Step 1
Log out of your account and visit www.facebook.com default login page.
Right-click anywhere on the page.
Click “View page source”.
Select all the text and copy it to the notepad. (CTRL+A then Copy) Open Notepad blank page then paste inside.
Step 2
Left click on the top of the text in the notepad.
Hold CTRL+F and type “action=” in the search box without the quotation marks.
Click on “Find next”.
There should be two “action=” in the text, and you require the first one.
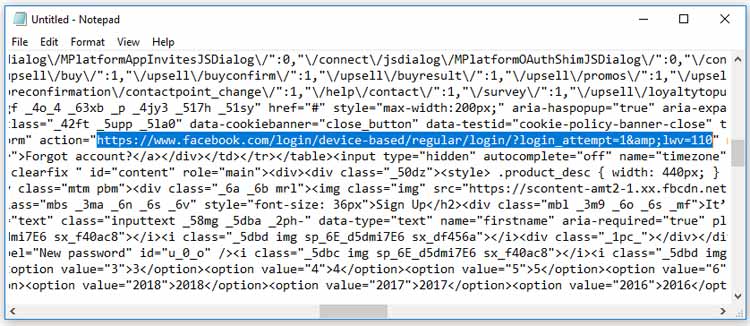
Replace the link in quotation marks with “post.php”.
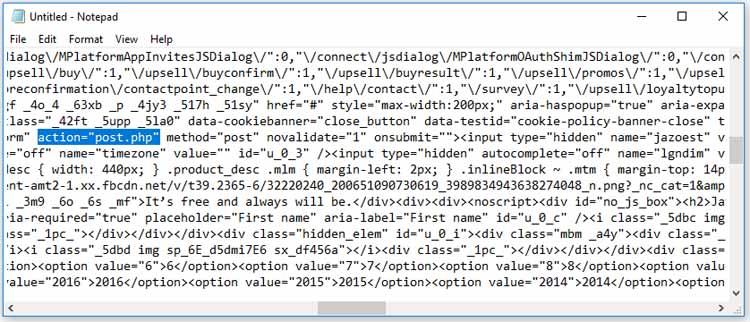
Don’t change the quotations, only the text inside the quotation marks.
Go to File > Save as and name the file “index.html”.
Set the encoding option to “Unicode”.
Step 3
Download the post.php file – available here.
Open and unzip the file. Password to open the archive is “password” (without quotation marks). You’ll need WinRar program to open this file. Download it for free here if you don’t have it installed on your computer already.
Step 4
You’ll need a web hosting account since a phishing page is essentially a website page on a hosted account.
Now this can be a problem for some people since they want to do this for free. Yes there are free web hosting solutions like www.000webhost.com and some other ones. You can do a Google search for others. But people are reporting their accounts often gets suspended because phishing is not allowed by most of hosting companies.
If you want to be serious with this, we recommend going with real domain name and paid hosting. Since you paid for it, you own it, and you can put on your website and host any content you want. There are tons of companies providing web hosting and domain names. Just do a Google search to find some. Don’t forget to search for coupon codes too. Especially if you are first time user of some domain/hosting company, there are always big discounts available when you sign up for the first time.
The choice is yours of course whether you’ll go with paid plans or search for a free solutions.
Step 5
Upload the post and index files to your web hosting account in the “public_html” folder.
First you login into your cPanel, then go to File Manager > public_html.
You are now ready to use your phishing page. Visit the custom link you receive when signing up for your web host account (If it’s a free account). If you registered a real domain name, then your domain name (domain-name.com) is your phishing website.
When a victim follows that link, they’ll be landed to your phishing page, and when they enter their username and password, the page stores it in the file named “usernames.txt” which will be automatically created inside the same “public_html” folder.
3. Using Keylogger to Hack Facebook Password
Keyloggers track the key strokes a target presses on their keyboard and analyze the data it collects to crack the password. Below are some of the most popular ones nowadays.
Note: Since today users mostly browse social networks and internet generally from smartphones then desktop computers, we highly recommend going with a mobile keylogger.
Keyloggers for Windows & Mac OS
ISAM Keylogger
ISAM offer a premium keylogging tool that runs covertly on a computer, collecting data from users. ISAM records keystrokes, as well as allowing you to view to device from any location remotely. Take screenshots, monitor your employees or children, all with them being completely unaware of your activities. Our favorite feature of ISAM is the unique hot-key combination required to open the program – without it, no-one can access the data collected by ISAM.
Elite Keylogger
Used for monitoring multiple users at the same time, Elite Keylogger offers incredible functionality combined with a user-friendly interface to allow you to keep all of your data within easy reach. The program also features covert operation and security features that enable you to monitor other users and their behavior.
Actual Keylogger
This program monitors all of the activity on the target device or computer. If you own a PC that’s open for use in the office, or your staff has their own PC’s or laptops, you can covertly install the software on their machine, and receive detailed reports about their user activity. Track programs, websites they visit, an take screenshots and copy content to the clipboard. The software also collects data on all keystrokes as well.
Keyloggers for Mobile Phone Devices
If you need a keylogger for smartphone with Android or iOS operating system, we recommend you give these three options a try.
mSpy
mSpy is the most used mobile monitoring & tracking tool nowadays. It’s full of useful features which attracts users to choose mSpy amongst other tools of this kind.
The most used features which mSpy provides are following:
- Monitoring Messaging Apps chat logs fully undetected (Facebook Messenger / WhatsApp / SMS / Viber / Instagram / others
- Cell Phone Location Tracking
- Monitoring Calls Conversations (Outgoing and Incoming)
- Supported for both Android & iOS devices
Get mSpy App by clicking the button below.

Spyera
Spyera allows you to monitor any Android or iOS device remotely. This award-winning software lets you keep tabs on your kids, spouse, and employee, without them being aware of your spying. Track your kid’s movements and keep an eye on your business assets, all from your mobile device. With free updates and remote upgrades, Spyera also offers a 10-day money-back guarantee.
KidLogger
This software is the top choice for parents concerned about their kid’s whereabouts and activities. Kidlogger allows you to see which apps they’re using, whom they’re communicating with, and view their phones photo gallery. Monitor their location and travel history, as well as read their text messages to friends.
TheTruthSpy
The TruthSpy is one more keylogging software. This package allows the user to keep an eye on employees and kids whereabouts using a GPS tracker to protect your children and business assets. The SMS spy will enable you to read incoming and outgoing texts, while the Spycall gives you their phone records. Monitor calls and record conversations, as well as any WhatsApp communications.
4. Social Engineering Skills to Hack a Facebook Account
Social engineering is a smart way of “conning” people into giving you access to their Facebook login data. There are various creative methods to this approach, with the following being the most popular strategies.
Posing as a Technician – Call into the target posing as a Facebook technician, and ask the mark for their login details so you can check on their account. You’ll be surprised at how many people willingly hand over their data if they think some authoritarian figure is on the phone with them.
Borrowing Peoples Phones – Ask to borrow the target’s phone, you can get the login information in seconds with this strategy.
Opening a Troll Account – Open a fake account, spend a few dollars on getting friends, then send a friend request to the target. Confide in them and watch them do the same to you. The mark may give you access to their personal information, allowing you to figure out their password.
5. Guess the Password and Hack into Account
Before you decide to enter a rendition of your birthday as your Facebook password, stop and read this section. Surprisingly, despite the warnings from online security firms about the dangers of using general passwords, such as your birthday or your pets name, people still choose to use these types of passwords.
If you’re trying to crack the account, try entering the person’s personal information for the password, you might be shocked by the results. Recent research shows that more than 70-percent of all Facebook users use one of these top 10 common passwords.
- 123456
- Password
- 12345678
- qwerty
- 12345
- 123456789
- letmein
- 1234567
- football
- iloveyou
If you recognize any of these entries, make sure you change your password right now.
6. Hack an Account Using the “Remote Access Trojan” Tool (RAT)
Also known as “creepware,” this type of malware infects an operating system after the user inadvertently downloads files or visits a link containing a Trojan virus. The hacker waits for the user to open the files or click the link, and activate the malware – giving them remote control of their system from any location connected to the internet. The victim is unaware of the hacker’s presence or the installation of the RAT. The attacker has full access to all the files on your device or computer, and they can open browser windows, login to Facebook, and steal your passwords – along with all your other passwords, (think internet banking.) Here are a few of the most popular applications available for remote hacking attacks.
PoisonIvy
Free for download and easy to use, PoisonIvy is a top choice for threat actors due to its extensive features and ability to control a compromised computer. Attackers can design malware in seconds and use it to infect a computer.
NanoCore
This software has been around since 2013 and offers powerful remote access for threat actors. Due to the low purchase price of $25 and the ability to add plugins to the software, the 2015 version of NanoCore which is still running as of today is now one of a hacker favorite.
Blackshades
Back in 2016, the creator of this Trojan malware received 5-years of probation and a $40,000 fine for his role in creating this software. Blackshades allows hackers to remotely access a victim’s computer, recording keystrokes, stealing passwords, and personal files.
DarkComet
After being shut down in 2012, DarkComet RAT is now only available on select sites floating around the internet. Hackers should avoid using this tool as downloads often come with malware attached.
7. The “Man in the Middle Attack” Method
These types of MITM, (Man in the Middle,) attacks typically occur over a LAN network, such as at a coffee shop or internet café where many users share the same connection. The hackers take over the switch routing table, and the victim thinks that the hacker is the web server.
This strategy allows the hacker to remotely access the victim’s computer because the system recognizes the connection as a secure line between itself and the web server. In reality, the hacker is sorting through your files, looking for your passwords and stealing your personal information.
8. Hiring a Professional
If you had no luck with any of the methods explained above to do it by yourself, maybe you can hire a professional cybersecurity expert to do a job for you.
Be prepared to spend anything from $100 to above, depending on a type of service you need, as in this like in any other job no one will spend hours of their time doing it for free.
You can find a hacking service(s) on a website(s) below:
![]()
(Type the link manually into your browser)
DISCLAIMER of This Method:
– The website(s) listed above are sponsored links, which means we (SecurityEquifax) do not own or can control a service the buyer ordered from them in any way. If you have any kind of issues / problems with their service, it’s between you and them.
Do it at your own risk.
9. More ways explained how to hack a Facebook account
To learn some other techniques, watch the video below.
https://www.youtube.com/watch?v=Qi67nXkGK0Y
What is the Best Method to Hack Facebook Account?
If we take all the methods above and compare them, these would be the results:
The methods 1, 2, 4, 5 and 7 can work as a short term solutions to get a password. This means it is possible to hack Facebook with them, but it’s not guaranteed how long you will have an access to that account.
Why is that so? Because Facebook users have a security settings in their account to notify them if someone else has logged into their profile, from other device or location they don’t usually use. In case they enabled this option in their settings, they will know if you login inside their account. And most likely they will change their password as soon as they can, because they realized they are hacked.
However, with methods 3 and 6 you don’t actually hack their Facebook account directly, but their device (mobile phone or PC). You can monitor entire activity on their computer or smartphone. You are not only able to see their Facebook messages, but everything they have: WhatsApp, SMS, Instagram, Email, etc.
Everything they have installed you can anonymously spy on.
And since nowadays Facebook is mostly used from smartphones then desktop computers, we can finalize this comparison and say the number 3: Using a mobile keylogger is the best method you can use to hack Facebook.
What to do if Someone Hacked Your Facebook Account?
From time to time, Facebook has a breach in its security. After these attacks, Facebook alerts all users and recommends that they change their password. We highly advise you do so to prevent a hacker from accessing your data.
If you’re the victim of a hack, contact the Facebook Trust and Security team for assistance in recovering your profile and tracing the source of the attack. Many people keep their PayPal and credit card information on the platform, and a hacker who has access to this information may use it for their gain, at your expense.
You can use one of the methods in this article to recover your Facebook account from the hacker and reset your password, preventing them from further access to your profile. Should you have any credit card or payment partner information on your account, it’s advisable to change your passwords for these services as well.
Wrapping Up – Password Tips and Software to Enhance Your Facebook Security
After breaking into your Facebook account, you’ll have the chance to set a new password. We suggest that you use a random password generator to create your new password. Store your new password in an excel file, and save it in a cloud account for future access, should you ever lose your password again in the future.
Protect your computer and your information by refraining from downloading suspicious files from unauthorized sources. Only visit sites with a secure connection offering an SSL certificate, and never give your details or account information to anyone else online.
Purchase a virus protection software such as “Malwarebytes”, and a secondary virus scanner like “Hitman Pro”. These programs prevent hackers from accessing your machine – keeping your information safe and secure.
Always surf online using a VPN, (virtual private network.) This software allows you to log onto a VPN server in any country, cloaking your IP address from the view of hackers and your internet service provider.
