
Many internet users across the world got themselves in situation of losing their account password at least once in their lifetime. This problem may occur due to many reasons. One can simply forget or save their password somewhere safe, and after some time you can’t remember it. Some Twitter accounts are also getting hacked, stolen and lost forever.
In most situations, a simple clicking on “Forgot my password” button on Twitter’s login page will solve a problem – In case you still have access to an e-mail account used when creating your TW profile. Same is with phone number verification.
But the problem occurs when user forgot even their registration email along with password together. And they didn’t add a phone number to their Twitter account, or they’ve changed it in meantime. If you recognize yourself in this one, then a Twitter support won’t be a solution to rely on. They will always ask you to verify you’re an actual account’s owner by providing an email address ID used when signing up for a certain account you’d like to recover, or do a SMS verification.
But even in these situation, there is still a hope to recover your account back.
In today’s article we’ll to show you several working methods to hack a Twitter account even if you don’t have access to an email address used when you registered your profile.
Disclaimer of This Tutorial:
Due to potential risks of misusing information from this tutorial in wrong ways, such as hacking Twitter accounts which are not in one’s legal ownership, we are obligated to protect ourselves and our website from any illegal use of the information we share here. That means it’s strictly forbidden to hack into Twitter accounts which you didn’t create by yourself, or without an actual owner’s prior permission to do so. Anything else will be tolerated as against our terms & conditions policy.
The working ways to hack into a Twitter account
– Quick Jump to the methods:
1. Using TWGrappler App
2. How to hack Twitter account using phishing
3. Using a Cell Phone Spying App
4. Hire a professional hacker online
1. Using TWGrappler App to hack Twitter Password
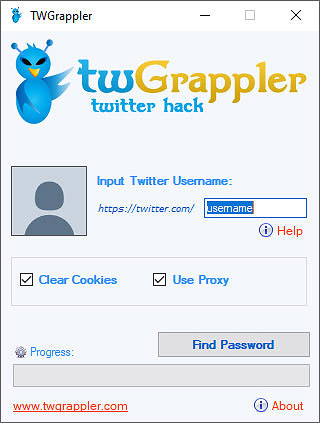
TWGrappler is one of the newly made application built just for this purpose. To help Twitter users recover access to their lost account when no any other methods works.
A technology which TWGrappler is built on is called a “brute-force attack”. This is relatively an old hacking method what requires a specially created program which attempts to login with thousands of possible password combinations until it finds a right one.
TWGrappler is using its own customized version of brute-force technology which functions together with proxy system. This enables the application to attempt to crack password with unlimited times without getting blocked from Twitter’s security system. Normally Twitter will temporarily block any IP address if someone failed to login three time in a row to a certain account. But with using this proxy system TWGrappler will automatically change IP address to a new one every third unsuccessful attempt. This way it can run unstoppable until it hacks and find a right password of entered account.
You can use TWGrappler App on any modern device, including desktop computers and smartphones.
Supported operating systems are Microsoft Windows, macOS, Android and iOS.
Currently Linux is not on the list, but developers claims they’re working on supporting their software for this OS as well.
Download TWGrappler App at:
www.twgrappler.com
2. How to hack Twitter account using phishing technique?
Even this method is dating back to 80’s, phishing is still remaining popular technique amongst hackers as of today.
This is a technique which requires skillfully use of social engineering skills and a medium knowledge of HTML programming language. Some CSS and PHP knowing will come helpful too.
So, what exactly phishing is?
It’s a way to trick someone to login trough a fake webpage which is made to look like a legitimate website. In our example we talk about Twitter, but phishing is also widely used for any other popular websites, like Facebook, Instagram, email accounts, bank accounts, credit cards details etc.
First step would be to create a fake Twitter login website. We won’t teach you step by step here how to make one as that would be unauthorized by law and can lead us to legal problems. But we can guide you approximately how you can learn by yourself to make one, for educational and entertaining purpose only.
Maybe you can find some pre-made ones which are ready to use on internet already. But you’ll have to search that by yourself. Or you can pay some web developer to make you one.
But shortly, you start with going to Twitter’s login page, where you can see boxes to enter username and password. When you’re on that page, go to website source by clicking right click and then “View Page Source”. You can also use a shortcut CTRL+U on your keyboard.
Next step is to copy everything you see in page’s source and paste it into a blank Notepad document. Before saving a file, you’ll have to edit a code to replace links which leads users entered information (username & password) from Twitter’s server to your own one which you’ll have to register later.
You can look at example from how to create a phishing page for Facebook which we explained before, and just do it in a same way for Twitter.
After you are done with creating a Twitter fake login page and have a website files ready on your PC, it’s time to register a hosting account and a domain what you will use for hosting your phishing page.
There are many companies where you can register domain and hosting, and many of them offers both together. If you are registering these for a first time, in most situations you can get a big discount for your first order so both will cost you just few dollars.
Some popular providers of webhosting + domain which we can recommend are:
BlueHost, HostGator, NameCheap, GoDaddy and many others.
Search their names on Google to find their website easily. And also don’t forget to search for coupon code as well which will reduce your order’s price drastically if you’re first time registering yourself there.
Tip when selecting a domain name:
– Make it something to look like Twitter official domain.
Examples (Didn’t check if they already exist): “twitterloginuser.com”, “twitter-users-login.com”, “login-twitter-webpage.com” or something similar. Make something by yourself which looks legit. Domain extension we recommend going with “.com” as that always looks most trustworthy. And because Twitter use it as well.
After you have your domain and hosting registered, it’s time to upload your files to your hosting account.
(Make sure your domain is pointing to your hosting by its nameservers or other DNS method. If you registered both at same company, this will be much easier to make.)
In your server’s cPanel account, go to File Manager, then look for “public_html” folder. In this folder you need to upload your Twitter fake page. If there is already a file named “default.php” before, delete it.
Now your phishing page should be ready for usage if you done everything correctly. Test it by going to your domain you registered by typing it into browser’s URL field. If a website is loading fine, you are now ready to use it to catch potential Twitter login credentials.
How to trick victims to login trough a phishing page?
You have to be creative here. Skilled hackers often make a trustworthy looking email address which looks like from original website’s company of which they’re planning to hack user.
For example, you registered a domain name for Twitter phishing let’s say “twitterloginpage.com”. Now you can also make an email address from this domain with any name you want. Let’s say “[email protected]” – Now if you have your victim’s email address, you can pretend you are an actual Twitter’s security agent and make your email massage to look like it’s official Twitter’s one. Example:
“Account Verification Required – Login trough our secured website here to confirm your account ownership” Then you link your phishing link with “here”. They will think it’s real, but at the end they will login trough your website and their Twitter password will be saved in a text file hosted at your newly registered webhosting account.
There are tons of possibilities how you can do this successfully. The key is to make something which looks trustworthy and legit. Think outside of the box and some good idea will always come.
3. Using a Cell Phone Spying App
If someone you’re planning to hack is using Twitter on their mobile phone, then the eyeZy app may be the best method listed here. Why?
By using eyeZy, not only you’ll be able to access their Twitter account, but hack their entire smartphone, without them knowing!
Let’s take a moment to see full features of eyeZy tool and what it’s capable of.
mSpy Features:
- Works on Android & iOS (No Jailbreak nor root system is required)
- Monitor All Messaging Apps Activity
(WhatsApp, SMS, Email, Facebook, Twitter, Instagram, Tinder, Snapchat, others) - Works in Stealth Mode, Not detected by phone’s owner
- Track GPS Location of a cellphone
- Track Calls (Outgoing & Incoming)
- View any documents / media files saved on a phone
Download eyeZy App:
Tap here to get the eyeZy App from its official website.
__
You might be interested:
How to Spy a Cell Phone Remotely Without Access – Tutorial
4. Hire a professional hacker online to do a job for you
If you have tried all the methods above and none worked for you like expected, or you’re just feeling lazy to do it by yourself, there is always an option to pay someone to do all the hard work for you.
Prepare to spend about few hundreds of dollars for their fee. Since hacking online accounts usually costs about $200 to $1k or even more USD, depending how demanding the work would be for a hacker.
Where to find a hacker to hack a Twitter account?
Hackers usually post their ads across deep & dark web forums, since it’s not legal to advertise these kind of services on usual news and social media websites.
One of our recommendations would be a cybersecurity company linked below:
![]()
(Type the link manually into your browser)
Disclaimer:
The Link(s) above are sponsored, which means that we (SecurityEquifax team) can not control a service ordered from them in any way. If you get any issues with their job, it will be between you and them.
__
Disclaimer of this tutorial:
Hope you learned something useful today. Remember to use these methods for legal purposes only. Hacking Twitter accounts which you didn’t create by yourself is a criminal act and prohibited by law in most, in not all countries. Your activities performed after learned from this tutorial will be your own responsibility.
