0patch experts recently came out with a micropatch designed to mitigate a previously unidentified zero-day loophole in Adobe Reader. According to experts, this vulnerability can be abused by cyber criminals by hiding malware inside corrupt PDF files.
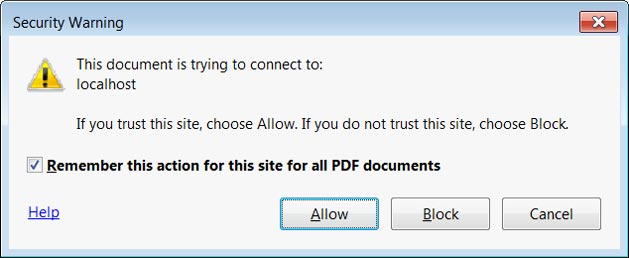
These documents would then transfer the target’s NTLM hash to the attacker through a SMB request. All of this can be done remotely which would make detection practically impossible.
The vulnerability was identified and reported by Alex Inführ, a security expert who also published a proof-of-concept and technical details of the problem. According to the report, the XML Form Architecture (XFA) structure was instrumental in crafting the attack. XFA is an integral part of PDF documents and it’s what Continue reading

 Intel users beware! Hackers have now discovered a new method to hide malware inside the security Intel SGX enclaves. Usually, the Intel Software Guard eXtensions (SGX) is a technology that’s used by app developers as a security measure against unwanted data modification or disclosure.
Intel users beware! Hackers have now discovered a new method to hide malware inside the security Intel SGX enclaves. Usually, the Intel Software Guard eXtensions (SGX) is a technology that’s used by app developers as a security measure against unwanted data modification or disclosure.




 A privilege escalation flaw has been discovered which could affect the online safety and privacy of LG laptop users. According to the online security expert who discovered the flaw, this loophole is relatively easy for hackers to take advantage of.
A privilege escalation flaw has been discovered which could affect the online safety and privacy of LG laptop users. According to the online security expert who discovered the flaw, this loophole is relatively easy for hackers to take advantage of.